How to: Managing Fine-Grained Password Policy in Server 2008
In this block I will explain and demonstrate the Fine-Grained Password Policy feature offered from Windows Server 2008 Active Directory.
From the earliest time of the Active Directory era, I have often been wondering why Microsoft made the password policy so inflexible: One domain, one Account policy (Password, Account lockout and Kerberos policy). This meant that if you needed more dedicated Account policies to different kind of employees; managers, administrators, standard users etc., you had to implement more than one domain in your enterprise, and that would generally result in more administration and a higher TCO.
To solve this issue, Microsoft introduced Fine-Grained Password policy in Windows Server 2008 Active Directory, which offers the ability to apply dedicated Password and Account Lockout policies to Users and Groups – not to OU’s unfortunately.
The requirement for using Fine-Grained Password policies is that the Domain Functional level is at least Windows Server 2008, and therefore all Domain Controllers in the Domain must at minimum be Windows Server 2008.
Fine-Grained Password policy is not configured through a Group Policy Object, GPO, where you traditionally configure Password and Account Lockout policies for the domain. Instead Fine-Grained Password policy is configured by creating an object in Active Directory called Password Setting Object (PSO). When you have created a PSO and configured the Password and Account Lockout settings, you can apply the PSO to users or groups in your domain.
As seen before when Microsoft introduce new features, the configuration of the Fine-Grained Password policy isn’t as smooth and straightforward as you might wish. In Windows Server 2008, you need to use the ADSIEdit console to create a PSO. Alternatively you can use PowerShell or third-party tools. In Windows Server 8 Microsoft has addressed this issue by making the creation and configuring available through the Active Directory Administrative Center. I will demonstrate this in a future blog.
In the following you can see the steps needed to create and configure a PSO in a Windows Server 2008 or Server 2008 R2 domain.
1. First you need to raise the domain functional level to at least Windows Server 2008. From the Active Directory Users and Computers console, right-click your domain and select Raise domain functional level…
2. Be aware that when you raise the domain functional level it is not possible to revert the action.
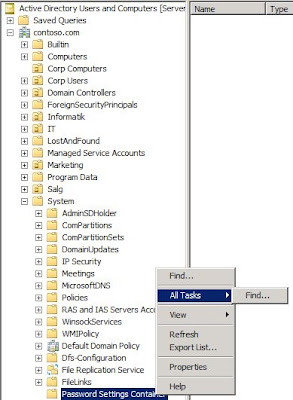
3. If you select the Advanced Features from the View tab in the console, you will now see the System part in the domain tree and in this section you can view and apply your existing PSO’s to users and groups. As you can see, it is not possible to create a PSO from this view. To create a PSO, you need to open the ADSI Editor.
4. In the ADSI Editor you first need to make an active connection
5. In this example I just make a default connection to the domain controller I’m logged on to.
6. As you can see, the structure is exactly the same as in Active Directory Users and Computers console, but in the ADSI Editor the structure is listed by the Distinguished Names. When you expand your domain and the CN=System container, you can right-click the CN=Password Setting Container and select New – Object…. This is where you create a new PSO. This will launch a wizard that will take you through the configuration of the password and account lockout settings you need to apply to a specific user or group.
7. First you need to give your PSO a descriptive name that you can relate to in the future. Design a good naming convention for your PSO’s before you create the first one.
8. Then you need to assign the PSO a precedence value, where 1 gives the PSO the highest priority in the case when a user is member of two groups which has both applied a PSO. Plan carefully the precedence values in your PSOs.
9. Normally you will not enable the reversible password encryption unless you have specific applications that need the reversible encryption enabled (the settings are true or false).
10. Here you define the password history
11. Then you enable or disable the password complexity (the settings are true or false).
12. Then you define the minimum password length.
13. The time format for the minimum password age, and all other time definitions is in the format of d:hh:mm:ss (days, hours, minutes, seconds).
14. Then you configure the maximum password age
15. Here you configure the lockout threshold value, defining the numbers of invalid logons before the users gets a lockout.
16. The Observation value represent the time elapsed after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts.
17. The Lockout duration value determines the time a lockout account remains locked out before automatically becoming unlocked. If you set the account lockout duration to 0, the account will be locked out until an administrator unlocks it. The Lockout duration value must be equal or greater than the Observation value described in the previous step.
18. When you have finished the wizard, you can see and edit the PSO from either the ADSI Editor or from the Active Directory Users and Computers console.
19. To apply the PSO to a user or group, right-click the PSO and select Properties. Select the Attribute Editor and scroll down to the msDS-PSOApplies To setting and click on Edit.
21. Here you can choose to locate the account either from direct search in the directory, or by specifying the account by its distinguished name. In this case I choose to apply the PSO to the IT Mangers group.
22. When look at the It Managers group properties sheet, and select the Attribute Editor, you can view or edit the msDS-PSOApplied attribute. You need select the Backlinks filter option first.
23. In this case Tom Heddelberg is a member of the IT Mangers group.
24. If you look at the Attribute Editor in Tom Heddelberg’s properties, you can see the applied PSO in the msDS_ResultantPSO attribute. You need select the Constructed filter option first.
25. To search for an applied PSO to a specific user you can use the dsget command utility, but the output only shows the applied PSO and not the specific settings in the PSO
26. If you use the Get-ADUserResultantPasswordPolicy cmdlet, you can see the applied PSO plus the actual settings applied.
Summary
The Fine-Grained Password Policy offered from Server 2008 Active Directory gives you the possibility to make more dedicated password and account lockout policies in your enterprise. But you need to be strict in your design and planning, because the PSO will have an immediate and enforced effect.
An advice could be, that you use the GPO based password and account lockout policy for all standard users in your enterprise, and dedicated PSOs on more restrictive accounts according to their group membership.

























No comments:
Post a Comment